-
How do blockchains use private and public key cryptography?
 linkweb3
linkweb3 2022-12-12
2022-12-12 3863
3863 Tech
Tech
-
Summary:How do blockchains use private and public key cryptography? The private key is confidential and used to sign a digital transaction to ensure that the source of the transaction is legal.
How do blockchains use private and public key cryptography? Use the public key and hash functions together to create a public address used to send and receive funds for cryptocurrency users. The private key is confidential and used to sign a digital transaction to ensure that the source of the transaction is legal. It is important to understand the importance of private key and public key cryptography in the blockchain. The following discussion is encrypted by private key and public key in the blockchain.
What is public key cryptocry?
Public key encryption is a security protocol that ensures the security of data exchange data in transactions in the blockchain network. In terms of security, it is essential in point -to -point networks like blockchain. Because in such a network, nodes do not know and trust each other. Need a powerful security system. A method that protects them from sending or receiving without worrying about security loopholes. In addition, this eliminates the needs of all nodes to understand and trust each other in person.
Public key code is an asymmetric type of cryptographic. We use a pair of key (public key and private key). It uses them to encrypt/decrypt information and verify users. The process of public key encryption ensures two things, namely:
1. Use the (receiving party) public key to encrypt information at the sender side. This ensures that any third party cannot access or understand encryption information inside and outside the Internet. Only expected recipients can use their private key decryption and reading messages.
2. Use the sender's private key to sign the message or information for verification. This verifies the identity of the sender and declare that he is a legal node in the blockchain network. The receiver uses the sender's public key to verify it. The verification process of users in the network is completed through digital signatures.
Therefore, public key code is a method to provide users with a digital identity. Safety transactions can be performed in the blockchain network. Let us know how to happen exactly now.
There are three key elements in public key cryptography, namely (i) key pairs; private and public keys, (ii) encryption wallets and wallet addresses, and (III) digital signatures. Each of these three elements has made significant contributions to creating a real digital identity, just like our bank account, account, and password. The only difference here is that it exchanges information or cryptocurrencies in the blockchain network.
Public key cryptography uses special algorithms to create these keys. These algorithms work in one way, that is, the algorithm will first create a private key, a public key, and then create a public address. We cannot reverse the generation order, that is, we cannot calculate the private key from the public key or calculate the wallet address from the public key.
This guarantees the security of the public key password system. This is because the public key and the public address are open for transactions and verification.
Therefore, the public key password guarantees the integrity of the information, the authenticity of the user, and the legality of the transaction. The private key is like a user's account password. People can decrypt the encoding messages sent to them and generate digital signatures to verify.
The public key is open to the network, and others use it to verify transactions and encryption messages. Therefore, whenever the two nodes are traded, the private and public keys of the two nodes are involved in ensuring the safety of transactions. It realizes this through encryption information and authenticated the user by the user's digital signature. This dual protection makes public key cryptography the best security system for blockchain.
Why do we need public key cryptography?
In the symmetrical key password, a single key is used to encrypt and decrypt messages. Here, the possibility of data loss or unauthorized access data is high. In order to overcome unauthorized data access and data sent by securely without causing any losses, we use public key crypto.
Public key encryption is safer than the allegy key encryption, because the public key uses these two keys to encrypt and decrypt the data
Public key encryption allows users to hide the data they want to send. The sender encryption data and the receiver decrypt the data. Unauthorized users cannot understand encryption.
Blockchain application of public key cryptography
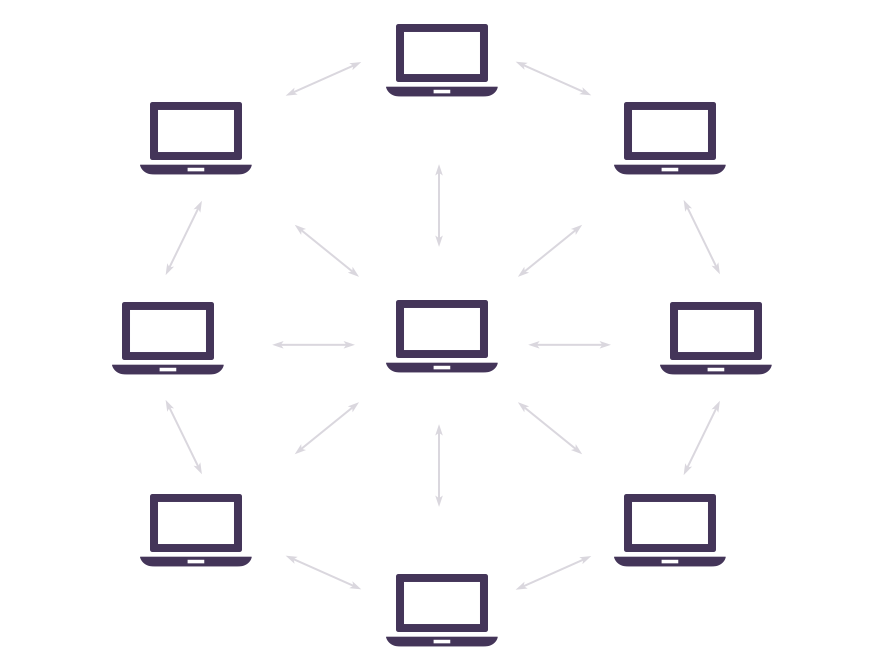
The blockchain is designed as a distributed and decentralized system. Each node in the network is responsible for maintaining a copy of their digital classification accounts, and data (in the form of transactions and blocks) transmits them between nodes through peer networks.
Public key encryption and digital signatures are essential for the system to work normally. They provide the following functions in the blockchain:
Identity verification: Digital signature certificate can only be created by those who know the corresponding private key. Since the public key links to a specific account, this ensures that only those who know the private key of the account can create a transaction from the account
Potal protection: Trading or blocks may pass multiple different nodes on the path from its creators to the network. Because the blockchain aims to maximize the trust of other nodes, it is necessary to protect this data from maliciously modified. Digital signatures are only valid when the relevant data is not tampered with, so that it can provide authentication and integrity protection
Identity management: On the blockchain, use public key cryptographic management identity. The account address is based on the public key, so creating a valid account only needs to generate a pair of private key/public key and related addresses. This enables blockchain users to maintain anonymous (private key is a random number that has nothing to do with its true identity), and at the same time ensure that any transaction used by the account is authorized (because they have effective digital signatures)
The benefits of public key cryptography
Public key cryptography promises to provide many security advantages in open networks like blockchain. The three most important aspects, as well as the advantages of using public key encryption as a security method: confidentiality, integrity and authenticity.
1. Secret: Blockchain uses a pair of key to ensure the confidentiality of the data we share. Mutual links and private keys ensure that the data or information we send is confidential. It decrypts the secrets by using the public key encryption data and using its corresponding private key to maintain the confidentiality.
2. Integration: Public key passwords also encrypt the data to maintain the integrity of the data. Due to terminal encryption, no one can access the information except the sender and the receiver. Therefore, it can be determined that the data is complete and no one has changed it in the middle.
3. Reality: Another important aspect and main advantage of public key encryption is the authenticity of the user. Because it uses a digital signature in each transaction, some people cannot forge their identity. This is why each node on the blockchain network can determine that the sender is the real part of the network. This is how the blockchain builds trust between its users.
The limitations of public key cryptography
Just as there are shortcomings, there are some limitations of public key cryptography.
1. Mathematical algorithm plus the ability to decrypt data or messages is limited to a certain size data. If there is a lot of data to be encrypted, the algorithm runs slowly. This will slow down the encryption process and require greater computing power.
2. If someone gets a secret private key or accidentally exposes it in the network. All data encrypted by this private key will fall into the hands of bad guys. Once the private key is leaked, the data cannot be restored or re -encrypted.
3. If a node loses its private key, its data will always be stuck, and they cannot be traded again from the same public address. Such nodes will not be able to access data encrypted by their private key.
What is a private key cryptography?
This is an important suggestion to remember: Do not share your private key with anyone. The private key enables you to prove ownership or spending funds related to your public address. The private key can adopt a variety of forms: 256 binary codes with lengths, 64 -bit hexadecim code, QR codes, and help words.
Regardless of its form, the private key is an astronomical figure, and it is very large. Although you can use a private key to generate a public key, the opposite method is almost impossible due to one -way "trap" function. You can connect any number of public keys to the private key.
The private key is a long string of alphabetic characters, which is unique for each user or node in the blockchain network. The private key is like a password. If it is shared, it can leak our confidential information. Therefore, we must keep our private key to the Internet.
Digital wallets (software or hardware) essentially store private keys because its security is very important. The common format of the storage key is the input format of the wallet, which has a 51 -character key. This length may vary from storage format.
The two main functions of the private key to provide security in the blockchain network are:
1) The private key key cryptography is used to decrypt the message of the (receiver) public key encryption. This ensures that the scheduled recipients get the news of encryption and are safe to other users on the way. Once the news arrives in the receiver intact, he uses his private key to decrypt it into a readable format.
2) Another important function of the private key key cryptography is to protect messages or information through digital signatures. Digital signatures are used to verify blockchain transactions. In the digital signature, the message is signed by the sender's private key. In this way, the receiver can verify the message (the use of the sender's public key) is actually sent by the sender rather than others.
Where is my "private key cryptography"?
Your private key key cryptography is located in cryptocurrency wallets, usually moving or desktop software or special hardware devices. Your private key key cryptography is not on the cryptocurrency blockchain network. If you store cryptocurrencies on the exchange, the exchange is the custodian of your private key; you use your key to trust it, just like your vaults you trust the bank to store your gold.
If you transfer cryptocurrencies from the exchange to a non -hosting wallet, then you can control your key. Due to the configuration and functions of cryptocurrency wallets, you may never handle private keys directly, because wallets usually manage them automatically. Usually, you will get a note with your private key key cryptography as a backup.
Public key and private key cryptography
The private key key cryptography used in the public key key cryptography is a random number with specific attributes (length, element, etc.). The public key key cryptography was assigned from the private key key cryptography.
The security of public key cryptography is based on mathematical "problems". This is an operation that performs "easy" (polynomial complexity) and reverse "difficulty" (index complexity). The commonly used "hard" problem includes:
Factor decomposition problem: Two prime numbers are multiplied by "easy", and "difficult" decomposition of "difficulty"
Discrete number problem: take the power "easy", "difficulty" for numbers
The difficulty of the problem is essential for the balance of safety and usability. Because some operations are easier than other operations, a algorithm can be designed to allow legitimate users to perform "simple" operations, and at the same time forced attackers to perform "difficulty" operations. By increasing the size of the value, the difficulty of adjusting the problem can be adjusted so that the system is available but not attacked.
How does private and public key cryptography work?
There are two main cases of public key encryption -identity recognition and confidentiality. In simple terms, you can describe it in the following way:
The sender obtained the public key of the recipient.
The sender uses this key to encrypt the information.
The sender sends the encrypted information to the recipient.
The recipient uses him or her private key to decrypt the data.
When it comes to cryptocurrencies, the private key is what you actually have. It proves that you have the right to manage your digital assets and authorize any transactions. Those who know this key can use related funds.
Advantages and limitations of public key and private key cryptography
There is no perfect method or encryption, including public key and private key. The following are advantages and disadvantages:
Advantage
The use of private key encryption technology is an excellent way for any company to protect important information. Whether you choose symmetrical or asymmetric encryption methods. Like any other technologies, they have their own advantages and disadvantages.
However, symmetrical encryption is faster and easier to execute. The system executes a single, reversible mathematical equation to encrypt or decrypt files. This is why this method requires less computer resources than non -symmetrical encryption.
At the same time, although the private key encryption provides a higher level of security, there are still some setbacks. The main problem related to this method is the problem of key transmission. It involves unsafe communication forms to transmit the key. It is risky to allow third parties to obtain unlocking data. This method cannot guarantee the source and authenticity of the message. If there is controversy or doubt, there may be some problems.
If users want to separate data or funds, they need to generate and manage multiple private keys. Too many keys are not so convenient, and sharing new keys with each party may increase insecurity.
Shortcoming
The disadvantages of this method are related to some serious weaknesses. First, the loss of private keys will lead to bleak consequences. This means no one can decrypt the received data. As far as cryptocurrency is concerned, if the private key is lost, the wallet owner will not be able to access him or her wallet.
Public key and private key cryptography control your cryptocurrency
How the public key and private key work are the basis for understanding how cryptocurrency transactions operate. When you say you have cryptocurrencies, what you really say is that you have the private key to prove the ownership of the cryptocurrency. Since it is stored on the blockchain, anyone can use your public key to verify that you are the owner.
The above introduces the relationship and difference between the crypto public key and the private key, as well as how to use them. Public key encryption helps users to maintain a reasonable security practice, because no one knows the private key to match the public key. Avoiding potential interception and cyber fraud is beneficial. However, all you need is to ensure that your private key is safe and others cannot access it. In the end, it is important to emphasize that you must keep your private keys or assistant words, or keep confidential at the same time. Stay it down and store it in multiple places, because if you lose or fall into the hand of the bad guy, it will not be recovered.
Disclaimer:As an open information publishing platform, shilian only represents the author's personal views and has nothing to do with shilian. If the article, picture, audio or video contains infringement, violation or other inappropriate remarks, please provide relevant materials and send it to: 2785592653@qq.com.
Hint:The information provided on this site does not represent any investment suggestion. Investment is risky, and you must be cautious when entering the market.
ShilianFan group:Provide the latest hot news, airdrop candy, red envelopes and other benefits, WeChat: rtt4322.