-
Why is a blockchain secure? The role of cryptography in blockchain secure.
 linkweb3
linkweb3 2022-12-21
2022-12-21 4059
4059 Tech
Tech
-
Summary:Why is a blockchain secure? Blockchain security is a comprehensive risk management system for blockchain networks, using network security framework, guarantee services and best practices to reduce attack and fraud risk.
Why is the blockchain safe? Blockchain technology is very safe in design. Blockchain security is a comprehensive risk management system for blockchain networks, using network security framework, guarantee services and best practices to reduce attack and fraud risk. Blockchain security is far from a simple topic. In this article, we will explore the security issues of the blockchain.
What is a blockchain?
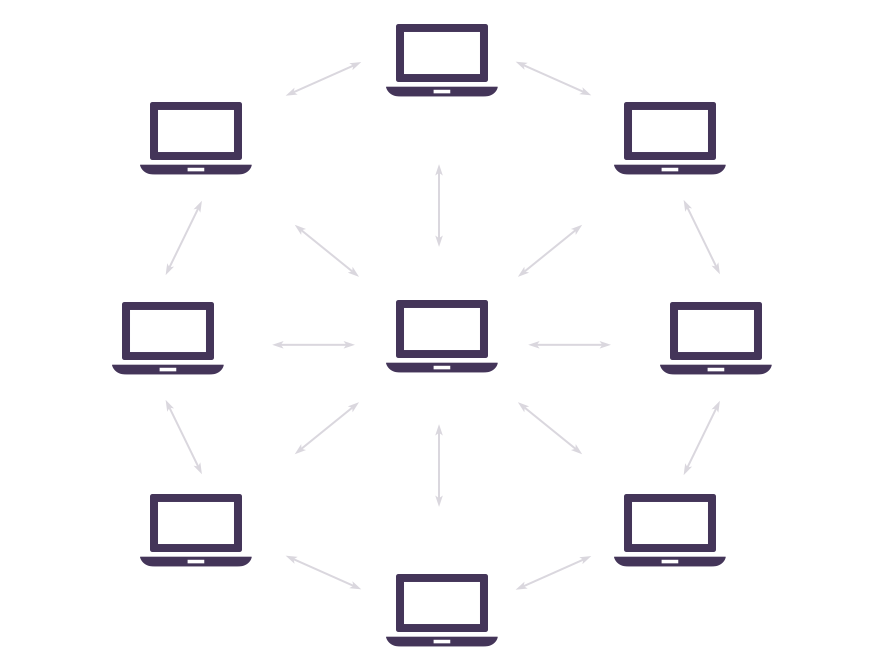
Blockchain technology produces a data structure with internal security characteristics. It is based on the principles of cryptography, decentralization and consensus to ensure the credibility of the transaction. In most blockchain or distributed ledger technology (DLT), the data is constructed into blocks, and each block contains one transaction or a group of transactions. Each new block is connected to all the previous blocks before the password chain in a way that is almost impossible to be tampered. All transactions in the block are verified and agreed by the consensus mechanism to ensure that each transaction is real and correct.
Blockchain technology achieved decentralization through the participation of members in a distributed network. Without a single -point failure, a single user cannot change the transaction record. However, blockchain technology is different in terms of key security.
What are the differences in the safety of the blockchain type
Blockchain network may be different in who can participate and access data. The network is usually marked as public or private (describing who allows who allows participation) and permits or non -allowable (describe how participants access the network).
Public and private blockchain
Public blockchain networks usually allow anyone to join and keep participants anonymous. Public blockchain uses connected computers to verify transactions and reach consensus. Bitcoin may be the most famous example of the public chain, and it reached a consensus through "Bitcoin mining". Computers on the Bitcoin network, or "miners", try to solve complex password problems to create work proof to verify the transaction. Except for the public key, this type of network has almost no identity and access control.
Private blockchain uses identity to confirm membership and access rights, and usually only known organizations are allowed to join. These organizations form a private, limited "commercial network". The private blockchain in the license network has reached a consensus through the process of "selective endorsement", and it is known that users verify transactions in the process. Only members with special access permissions can maintain the transaction classification account. This network type requires more identity and access control.
When building a blockchain application, evaluating which type of network is most suitable for your business goals. For compliance and regulatory reasons, private and licensed networks can be strictly controlled and prioritized. However, public and unauthorized networks can achieve larger decentralization and distribution.
Public blockchain is open, and anyone can join them and verify the transaction.
Private blockchain is limited, usually limited to commercial networks. Single entity or consortium controls member qualifications.
No blockchain has no restrictions on the processor.
The permitted blockchain is limited to a group of selection users who use certificates to be awarded.
Blockchain security: centralized block
As the name suggests, "blockchain technology" is a centralized digital blockchain containing trading currency. Each block is connected to the top and other blocks above it. Blockchain solutions are specially designed to prevent tampering and high safety.
Blockchain defines three core strategies: cryptography, decentralization and consensus.
All these measures make it difficult to use personal records to tamper with blockchain technology. This is because hackers need to change the entire block containing blockchain records. Network participants also allocate their security keys to the final trading key to act as personalized digital signatures.
In any case, if the record is tampered with, the digital signature will fail, and any attack will be immediately detected by the corresponding network.
Block safety
As the name suggests, the blockchain is a digital blockchain containing transaction records. Each block is connected to all the blocks before and after it. This makes it difficult to tampered with a single record, because hackers need to change the block containing the record and the block with their links to avoid being discovered. This one seems to have no great deterrence, but the blockchain has some other inherent characteristics, which can provide additional security methods.
The records on the blockchain are protected by passwordology. Network participants have their own private keys. These private keys are allocated to them and act as personal digital signatures. If the record is changed, the signature will fail, and the peer network will immediately know what happened. Early notification is essential for preventing further damage.
Unfortunately, for those ambitious hackers, the blockchain is scattered and distributed in the point -to -point network that is constantly updated and maintaining synchronization. Because they are not included in the central position, the blockchain has no single -point failure, and it cannot be changed from a computer. This will require a lot of computing power to access each instance (or at least 51%of the majority) of a blockchain and change them at the same time. Whether this means that the smaller blockchain network may be easily attacked, but it has not yet concluded. In any case, the larger your network, the more you fight against tampering.
At first glance, the blockchain has some ideal features that help protect your transaction data. However, when you want to use the blockchain for business, you need to consider other conditions and requirements.
Blockchain network is as safe as its infrastructure
When establishing a private blockchain, you must determine the best platform for deployment. Although the blockchain has the inherent attributes of security, the known vulnerabilities in your infrastructure may be manipulated by malicious people. Ideally, you should have an infrastructure with integrated security. This infrastructure can be:
Prevent anyone -or even root users and administrators -visit sensitive information
Reject illegal attempt to change the data or applications in the network.
Use the highest level of security standards to carefully protect the encryption key to prevent them from being stolen.
The role of cryptography in blockchain security
Blockchain is seriously dependent on cryptography to achieve its data security. In this case, the so -called encrypted scattering function has fundamental importance. Loltation is a process of receiving data input (distribution) that enjoys the data input (distribution function) that contains predictable and fixed sizes (or length).
Regardless of the input size, the output will always present the same length. But if the input is changed, the output will be completely different. However, if the input has not changed, the distribution of the generated will always be the same -no matter how many times you run the scattered function.
In the blockchain, the output values called the distribution are used as the unique identifier of the data block. The hash of each block is generated according to the hash in the previous block, which is why the linked blockchain is created. Block hash depends on the data contained in this block, which means that any changes to the data need to be changed.
Therefore, the hash of each block is based on the data contained in this block and the hash of the previous block. These hash standards play an important role in ensuring the safety and unsatisfactory of the blockchain.
Shadles are also used to verify the consensus algorithm of transactions. For example, on the Bitcoin blockchain, the workload certificate (POW) algorithm uses a hash function called SHA-256. As the name suggests, the SHA-256 accepts data input and returns a 256-bit or 64 character-length dissipation.
In addition to providing protection for transaction records on the classification account, cryptography also plays a role in ensuring the safety of storing wallets for cryptocurrency units. Public key and private keys that allow users to receive and send payments are created by non -symmetrical or public key cryptography. The private key is used to generate a digital signature for transactions, which can verify the ownership of the coin sent by the coin.
Although the specific details exceed the scope of this article, the essence of asymmetric cryptography prevents anyone other than the private key holder access the funds stored in cryptocurrency wallets, thereby ensuring the security of these funds until the owner decides to use them. (As long as the private key is not shared or leaked).
How safe is blockchain technology
The blockchain architecture behind modern cryptocurrencies, NFT and decentralized applications has important built -in security functions. Once the data block is added to the blockchain database, they are immutable. Hackers cannot change them to steal funds. The block is verified based on the consensus mechanism of eliminating fraud transactions and preventing hackers. The access to the database is protected by financial -level public key encryption. These functions make the blockchain architecture occupy a place in the safest database ever.
However, despite this advanced technology, hackers and scammers still steal millions of euros each year. how can that be?
The answer is that the secure blockchain network is part of the ecosystem, and the strength of the ecosystem depends on the weakest link. The blockchain itself is safe, but the usual safety prevention measures are applicable:
Safety access your hardware: If you leave your desk when you log in to your encrypted wallet at PC, anyone can quickly transfer all your cryptocurrencies to another account. Because the blockchain account is anonymous, you are likely to never know who it is, and you will never recover your cryptocurrency.
Protect your password: If you use a password in a file stored on the hard disk drive on the hard disk drive to protect your encryption wallet, then you will cause disaster.
Choose your trust application: If you use the new decentralized financial application that has not been tested, hackers may use the loopholes in the application code. Check them before entrusting your cash to DEFI applications. Who is behind them? How long did they run? How big is the user base? These problems can help you find mature and professional maintenance applications.
Holding skepticism: Some of the largest and most infamous scams in the encrypted world are to raise the shipping plan, of which scammers launch tokens or create temporary prices on social media -then quickly sell and exit the market, let buy to buy to buy to buy to buy to buy to buy to buy to buy to buy to buy it. The asset held by the home is not worth the token. These scams are targeted at the victims who are anxious to profit, and they will not ask the sudden price rise and whether it reflects the true value of the coin.
How to improve your blockchain security
In view of the fact that blockchain security issues do exist, individuals and enterprises should build their own blockchain security infrastructure from the inside to the outside to protect their blockchain activities.
This is to understand network threats related to blockchain technology -and how to manage them. Adhering to the best practice of network security can also greatly protect the data we stored in the blockchain network.
For this reason, please consider taking the following measures to improve your personal blockchain security:
Use a virtual network to encrypted your Internet activities and avoid routing attacks.
Do not share your key with anyone to avoid being invaded by hackers.
Don't let your device be careless to prevent malicious actors from accessing them.
Understand how to find online fishing attempts by being alert or unfounded news.
Do not change the data in the blockchain so that your user permissions will not be revoked.
Our method stores our data continuously. Knowing how to ensure that your safety is not only the best practice, but also a top priority.
Frequently Asked Questions Answers of Blockchain Security
1. Is the blockchain safe?
Due to the anonymity and security function embedded in technology, it is difficult to destroy the blockchain.
2. How does blockchain improve security?
The blockchain is protected by advanced encryption to protect each transaction and exchange on the platform.
3. Why is the safety of blockchain important?
Blockchain security is committed to protecting encrypted assets and account information stored in your personal data, which is highly sought after today.
4. What is the safest blockchain?
Bitcoin blockchain is known as one of the safest blockchain.
The above content introduces what the blockchain is safe. By combining the use of game theory and cryptography, the blockchain can obtain high -level security like a distributed system. Then, the cautious balance between decentralization and security is essential to build a reliable and effective cryptocurrency network. Blockchain is essentially safe. However, due to the security defects elsewhere in the encryption ecosystem, the loss of encryption is still very common.
Disclaimer:As an open information publishing platform, shilian only represents the author's personal views and has nothing to do with shilian. If the article, picture, audio or video contains infringement, violation or other inappropriate remarks, please provide relevant materials and send it to: 2785592653@qq.com.
Hint:The information provided on this site does not represent any investment suggestion. Investment is risky, and you must be cautious when entering the market.
ShilianFan group:Provide the latest hot news, airdrop candy, red envelopes and other benefits, WeChat: rtt4322.